Article Under Review
Getting My Mobile device cybersecurity To Work
Attacking Encrypted Traffic The prospect will display an idea of tools and tactics which can exploit SSL/TLS channels and render encryption ineffective all through mobile device penetration testing.Gray-hat hackers may perhaps opt to reveal the security vulnerability privately to the organization or manufacturer without having publicizing the outco
The 5-Second Trick For Phone security audit
With timely and quick tips from this ebook, you can safeguard yourself with each of the cyber threats.[bctt tweet="I see #security as an evolutionary procedure, some thing #iterative, #imperfect and #polymorphous @jjx" username="appknox"]His e book nine Ways to Cybersecurity targets leading amount executives in enterprises within a quite simple and
The smart Trick of Professional phone hacker That No One is Discussing
At oral argument, it appeared that a vast majority of Justices believed the warrantless assortment of CSLI violated the Fourth Amendment. There appeared to be very little consensus, nevertheless, on how the Court should get there.Also, have a tour of your phone’s constructed-in instruments—you probably don’t should down load an advert-filled
The Definitive Guide to Mobile device cybersecurity
During the seventies, the Supreme Courtroom observed that there was no Fourth Amendment protection for checks specified to your lender or phone numbers dialed and transmitted to some phone enterprise. The reasoning of those instances has actually been prolonged to electronic information by The federal government as well as some lower courts.Formerl
 Jeremy Miller Then & Now!
Jeremy Miller Then & Now! Marques Houston Then & Now!
Marques Houston Then & Now! Freddie Prinze Jr. Then & Now!
Freddie Prinze Jr. Then & Now! Matilda Ledger Then & Now!
Matilda Ledger Then & Now!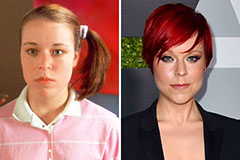 Tina Majorino Then & Now!
Tina Majorino Then & Now!